As digital products become more embedded in critical infrastructure and daily life, the maturity of secure development practices is under increasing scrutiny. The European Union’s Cyber Resilience Act (CRA) and related regulations such as NIS2 are accelerating the need for organisations to adopt secure-by-design principles. Yet, despite growing awareness, the maturity of secure development practices across industries remains uneven. This paper explores the current state of secure development maturity using OWASP SAMM benchmark data. It also examines how organisational size and sector influence readiness. As well as outlining how structured application security programs can close the gap between current practices and regulatory expectations.
Understanding the current landscape of secure development
The OWASP Software Assurance Maturity Model (SAMM) has become a widely adopted framework for assessing and improving software security practices. It evaluates maturity across five domains: governance, design, implementation, verification, and operations. According to the latest benchmark data, the average maturity score across organisations is 1.44 out of 3.0. This suggests that while many companies have initiated secure development practices, few have institutionalized them in a repeatable, measurable way.
A closer look at the data reveals that maturity levels vary significantly depending on the size and sector of the organisation. Large enterprises, particularly those in regulated industries such as finance and healthcare, tend to have more formalized governance structures and dedicated application security teams. However, they often struggle with scaling secure practices across complex, distributed development environments.
In contrast, SMEs are typically more agile and open to adopting modern DevSecOps tools, but they frequently lack structured roadmaps, dedicated security roles, and the resources to meet compliance requirements.
Public sector organisations and operators of critical infrastructure often show higher maturity in documentation and auditability, driven by regulatory mandates. However, they are also constrained by legacy systems and procurement cycles that can slow down the adoption of modern security practices.
Regulatory pressure: CRA and NIS2
The Cyber Resilience Act introduces a comprehensive set of cyber security requirements for digital products and services in the EU. And it applies to manufacturers, importers and distributors. These include the obligation to implement security-by-design and risk management, maintain continuous vulnerability handling, and ensure traceability of security measures throughout the product lifecycle, including proper documentation and communication to end-users.
The NIS2 Directive further extends these expectations to essential and important entities across sectors (such as energy, transport, health, digital infrastructure), emphasizing risk management, incident reporting, and supply chain security.
These regulations are not merely checklists—they require demonstrable evidence of secure development practices. Organisations must be able to show that security is embedded from the earliest stages of design through to deployment and maintenance or they will face high fines. This shift from reactive to proactive security demands a cultural transformation as much as a technical one, meaning structured governance and repeatable processes across the software lifecycle.
Beyond regulatory compliance, security is increasingly recognised as a cornerstone of quality and a critical market differentiator. Customers and partners are prioritising secure products and services, understanding the risks associated with vulnerabilities. Studies further underline the stakes. More than half of small enterprises that fall victim to cyberattacks are forced to close their doors within six months, highlighting the existential importance of proactive security measures.
Readiness gap
Despite the urgency and growing awareness, many organisations are still not yet prepared to meet the requirements of those regulations. One of the most common issues is the absence of a structured assessment of current practices. Without a clear understanding of where they stand, organisations struggle to identify improvements or allocate resources effectively.
The first step is to conduct a baseline assessment using maturity models like OWASP SAMM or BSIMM. This provides a clear picture of strengths and weaknesses across the organisation and helps identify gaps relative to regulatory requirements. Industry experts are currently discussing about how to use SAMM to identify compliance with regards to the CRA, and the first estimations are that, based on the benchmark data, most companies are not yet ready. This is even more true for SMEs, and they are also subject to the regulations.
Pro-tip: tools like SAMMY can help you keep track of your assessment and define targets. They also embed the expected requirements for CRA, allowing you to set objectives to reach compliance.,
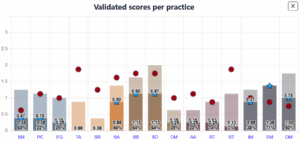
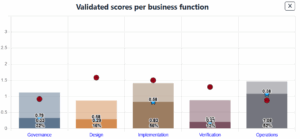
Figure 1– SAMM assessment and targets for CRA in SAMMY
Another challenge is the lack of consistent risk prioritisation. Security efforts are often reactive, driven by incidents or audits, rather than aligned with business risk and strategic objectives. This leads to fragmented initiatives that fail to deliver lasting improvements.
Developer enablement is also a critical gap. Secure coding practices are not consistently embedded into daily workflows, and training is often limited to one-off sessions rather than continuous learning. Moreover, security tools are frequently bolted onto the development process rather than integrated into the toolchain, resulting in friction and low adoption.
The need for a clear application security program
To address secure development maturity challenges, organisations need a structured application security program that is tailored to their context and maturity level.
Based on this assessment, a tailored roadmap should be developed. This roadmap should include short-term actions to address critical gaps, medium-term initiatives to build foundational capabilities, and long-term goals to institutionalize secure development practices. The roadmap must be risk-based and aligned with business and regulatory priorities to ensure executive support and sustainable investment.
Toolchain integration is important, and security checks should be embedded into CI/CD pipelines. This will enable continuous verification and traceability, with tools like SAST, DAST, SCA. However, as a tool is only as good as its user, developer enablement should be a central pillar of the program. This includes providing role-specific training, integrating secure coding guidelines into development workflows, and offering hands-on learning.
Finally, governance structures must be established to ensure accountability and oversight. This includes defining roles and responsibilities, setting measurable KPIs, and implementing dashboards to track progress. Regular reviews and updates to the program are essential to adapt to evolving threats and regulatory expectations.
Guidance to embed security as a strategic capability
In parallel, it’s important to acknowledge that not all organisations have the internal expertise or capacity to build and sustain a mature secure development programme on their own. This is particularly true for smaller companies or those in sectors where cybersecurity has not traditionally been a core focus. In such cases, partnering with external experts can be a pragmatic and effective strategy.
External organisations, whether specialised consultancies, security vendors, or industry alliances, can provide critical support in the form of assessments, roadmap development, training, standards, toolchain integration, and even interim AppSec leadership. These partnerships can accelerate maturity, reduce the burden on internal teams, and ensure alignment with evolving regulatory expectation. Importantly, they also offer an outside-in perspective that helps challenge assumptions and uncover blind spots that internal teams may overlook.
By combining internal commitment with external guidance, organisations can build a secure development capability that is both resilient and scalable, regardless of their starting point.
Conclusion
The convergence of regulatory pressure and increasing cyber threats makes secure development maturity a strategic imperative. Ultimately, achieving secure development maturity is not a destination but a continuous journey. Organisations must remain agile, adapting their programs by fostering a culture of security, investing in education, and leveraging both internal capabilities and external expertise and tooling. They can transform application security from a compliance obligation into a strategic advantage. This proactive approach will not only safeguard their operations but also inspire trust among stakeholders, demonstrating their commitment to innovation and resilience in the face of evolving challenges.
Looking for some help? Have a look at our Secure Developments Solutions.

